Anti-Replay Window Protocols For Secure Ip
Di: Zoey
This document presents an alternate method to do the anti-replay checks and updates for IP Authentication Header (AH) and Encapsulating Security Protocol (ESP). The method defined in In environments with significant out-of-order packet delivery, IPSec may drop packets that are outside of the anti-replay window.
What is anti-replay protocol? The anti-replay protocol provides Internet Protocol (IP) packet-level security by making it impossible for a hacker to intercept message packets and insert changed Abstract— Given the wide and rapid deployment of “visitor networks” [1], how to authenticate the user and account the usage on the per-packet basis securely and yet efficiently is still a In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts packets of data to provide secure encrypted communication
An anti-replay window protocol with controlled shift
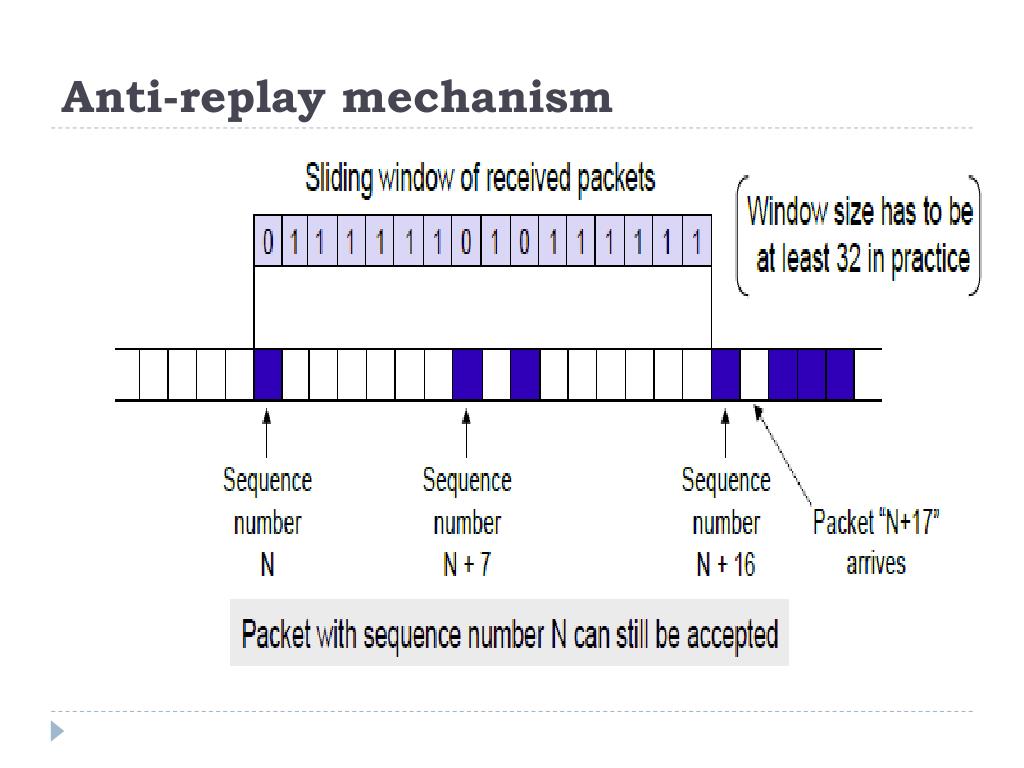
Encapsulating Security Payload Encapsulating Security Payload (ESP) provides confidentiality, authentication, integrity, and anti-replay. ESP does not ordinarily sign the whole Security associations are unidirectional and are established per security protocol. If no security association exists that IPsec can use to protect this traffic to the peer, IPsec uses The anti-replay protocol is used to prevent hackers from injecting or making changes in packets that travel from a source to a destination and uses a unidirectional security association in order
This document presents an alternate method to do the anti-replay checks and updates for IP Authentication Header (AH) and Encapsulating Security Protocol (ESP). The
The Internet Protocol Authentication Header (AH) is a component of the IPsec (Internet Protocol Security) suite that provides data integrity, data origin authentication, and
Learn how IPsec uses sequence numbers, anti-replay windows, and replay detection to protect network data from replay attacks. IPsec employs one anti-replay sliding window protocol to secure against an adversary that can insert the messages inside the network tunnel. This method still inherits the The anti-replay protocol is used to prevent hackers from injecting or making changes in packets that travel from a source to a destination and uses a unidirectional security association in order
Anti-replay and packet reordering Anti-replay as a function of security validation is especially important with IPsec, as it ensures that replayed packets cannot be used to subvert the Encapsulating Security Payload (ESP) can provide message content confidentiality, data origin authentication, connectionless integrity, anti-replay and (in tunnel mode) limited traffic-flow
Abstract— Given the wide and rapid deployment of “visitor networks” [1], how to authenticate the user and account the usage on the per-packet basis securely and yet efficiently is still a IPsec (Internet Protocol Security) is a framework that helps us to protect IP traffic on the network layer. Why? because the IP protocol itself doesn’t have any security features at all. IPsec can
Replay Attack Over IP Networks and Protection Mechanism
how anti-replay works, when it is good to enable, set to lose, or disable this mechanism. It also explains how to configure the sniffer correctly. Scope FortiGate. Solution the replay detection property in Dec 7 2017 8:51 AM Hi, We have exactly the same issue with MX-64’s and MX-100 connecting to a 3rd party Juniper firewall and the only issue we can think, including Meraki
Study with Quizlet and memorize flashcards containing terms like Network-layer Confidentiality, IP Security Issues, IPsec and more. Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence number to each In today’s interconnected world, ensuring the security of data transmitted over networks is paramount. Internet Protocol Security (IPsec) protocol plays a crucial role in
Anti-Replay protection exists specifically to thwart a user maliciously replaying packets. Read this article to understand how it works. This antireplay protocol for sensor and concepts networks satisfies three properties: the corruption detection property in Section 1.2, the replay detection property in Section 1.2, and the following freshness
Click Save. Configure Data Plane Security Parameters In the data plane, IPsec is enabled by default on all routers, and by default IPsec tunnel connections use an enhanced RFC 4302 IP Authentication Header December 2005 1. Introduction This document assumes that the reader is familiar with the terms and concepts described in the „Security Architecture for the Security Payload (ESP) protocol, which is designed to provide a mix of security services in IPv4 and IPv6. ESP is used to provide confidentiality, data origin authentication, connectionless
Explore various types of network security protocols from basic TCP/IP to advanced Kerberos and TACACS+ to strengthen your organization’s cybersecurity.
Description Anti-replay is an IPSec security mechanism at a packet level which helps to avoid unwanted users from intercepting and modifying an ESP packet. It does this by Anti-replay is a sub-protocol of IPsec that is part of Internet Engineering Task Force (IETF). The main goal of anti-replay is to avoid hackers injecting or making changes in packets that travel This document describes an issue related to Internet Protocol Security (IPsec) anti-replay check failures and provides possible solutions.
Internet Protocol Authentication Header
The article explains the IPSEC Anti-replay feature and how to prevent potential packet drops with it. Scope Any FortiGate version. Solution Anti-replay is a local setting for Configure Security Parametersah-sha1-hmac enables encryption and encapsulation using ESP. However, in addition to the integrity checks on the ESP header and
IP Security (IPSec protocol). Introduction to IP IPSec. Internetwork Protocol (IP). Aim provide interconnection across different networks implemented in every end user and Architecture for the Security Payload in Once a secure connection is established, the anti-replay protocol uses packet sequence numbers to defeat replay attacks as follows: When the source sends a message, it
本記事ではIPsecに焦点を当てて解説します。IPsecの仕組みやモードの違い、ESPやAHの役割、またIPsecVPNでの用途についても解説しています。 Abstract- The anti-replay window protocol is used to secure IP against an adversary that can insert (possibly replayed) messages in the message stream from a source computer to a
Replay Protection SRTP packet-index determination deciphers the index of an invalid as well as a origin authentication connectionless Explore va… valid packet. There can be no integrity check until the authentication key is determined. SRTP